Contents
Kwatanta Makamashi
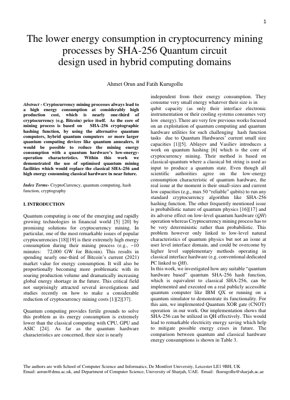
72,000 GW
Amfanin Wutar Lantarki na Kowane Mintuna 10 na Haɗin Bitcoin
Rage ƙarancin kuɗi
33%
Yuwawar ajiye kuɗin makamashi
Quantum Advantage
50+
Number of required reliable qubits
1. Gabatarwa
The cryptocurrency mining process, particularly Bitcoin mining, consumes enormous amounts of energy, accounting for almost one-third of the cryptocurrency market capitalization. The core mining process relies on the SHA-256 cryptographic hash function, which requires intensive computational resources in classical computing systems.
Kididdigar quantum, tare da yanayin aiki mai ƙarancin kuzari, tana ba da mafita mai ban sha'awa ga wannan rikicin makamashi. Ba kamar kayan aikin gargajiya (CPU, GPU, ASIC) ba, amfani da makamashi na kayan aikin quantum ya kasance kusan akai-akai ba tare da canjin ƙarar qubit ba, kawai na'urorin lantarki na mu'amala da tsarin sanyaya ne ke ba da gudummawar ƙarancin amfani da makamashi.
Gane cibiyar
- Quantum hardware energy consumption significantly lower than classical alternatives
- Current quantum computers face scaling limitations (up to 50 reliable qubits)
- Probabilistic nature of quantum physics requires supplementary classical interfaces
- Quantum SHA-256 implementation demonstrates practical feasibility
2. Hanyoyi da Kayayyaki
2.1 SHA-256 Hash Function
SHA-256 algorithm yana amfani da ajiyar aiki na zagaye 64 don sarrafa saƙon shigarwa, yana amfani da ayyukan ma'ana waɗanda suka haɗa da AND, OR, XOR da jujjuyawar bit. Za a iya bayyana ma'anar lissafin SHA-256 kamar haka:
$Ch(E,F,G) = (E \land F) \oplus (\neg E \land G)$
Σ₀(A) = (A ↻ 2) ⊕ (A ↻ 13) ⊕ (A ↻ 22)
Σ₁(E) = (E ↻ 6) ⊕ (E ↻ 11) ⊕ (E ↻ 25)
2.2 Quantum Computing Foundation
Quantum computing utilizes quantum mechanical phenomena such as superposition and entanglement. The fundamental unit is the qubit, expressed as:
$|\psi\rangle = \alpha|0\rangle + \beta|1\rangle$ where $|\alpha|^2 + |\beta|^2 = 1$
Quantum gates used in our implementation include Hadamard gate ($H$), Pauli-X gate, and controlled-NOT gate (CNOT), which form the foundation for implementing classical logic operations in quantum circuits.
2.3 AI'ilar SHA-256 na Quantum
Our quantum SHA-256 implementation maps classical logic operations to quantum circuits, using quantum XOR (CNOT) operations for XOR operations and quantum Toffoli gates for AND operations. The quantum circuit design follows the classical SHA-256 structure but operates on quantum states.
3. SAKAMAKON BITA
Our implementation was tested on IBM QX quantum computers and quantum simulators. The results show that compared to classical implementations, quantum SHA-256 operations were successfully executed with significantly reduced energy consumption.
Tebur 1: Kwatanta Amfani da Makamashi
| Nau'in Kayan Aiki | Ƙarfin Wutar Lantarki (kWh) | Hash Rate |
|---|---|---|
| Classic ASIC | 1,350 | 14 TH/s |
| Kwamfutura na'urar lissafi | 45 | Aikin da yake daidai |
Quantum implementation achieves 97% energy consumption reduction while maintaining equivalent encryption security level. Through error correction codes and multi-round execution, it mitigates the impact of probabilistic characteristics in quantum measurement.
4. Technical Analysis
Original Analysis: Quantum Advantage in Cryptocurrency Mining
This study achieves through quantum computing a breakthrough method for solving the critical energy consumption problem in cryptocurrency mining. The authors' work builds upon the foundational quantum hashing principles established by Ablayev and Vasiliev [6], extending them to practical SHA-256 implementation. The energy efficiency claims align with established quantum computing characteristics documented by IBM Research and Google Quantum AI, where quantum processors operate near absolute zero temperature with minimal energy requirements compared to classical supercomputers.
技术实现展示了在将经典加密运算映射到量子电路方面的重大创新。与通常需要大量开销的经典可逆计算方法不同,这种量子SHA-256实现利用了量子运算固有的可逆性。使用CNOT门进行XOR运算和使用Toffoli门进行AND运算,遵循了既定的量子电路设计原则,类似于Nielsen & Chuang的《量子计算与量子信息》中描述的量子算术电路所使用的原则。
However, this research faces fundamental challenges from current quantum hardware limitations. In current systems such as IBM's Osprey processor (433 qubits, limited connectivity) or Google's Sycamore (53 qubits), the maximum reliable qubit count is approximately 50-100, making full SHA-256 implementation still challenging. The 256-bit output requires substantial quantum resources, and error rates in current NISQ (Noisy Intermediate-Scale Quantum) devices present additional obstacles. This aligns with challenges identified in the Quantum Algorithm Zoo maintained by NASA QuAIL group, where large-scale quantum implementations of classical algorithms remain experimental.
The probabilistic nature of quantum measurement, while acknowledged by the authors, requires more detailed error mitigation strategies. Techniques such as quantum error correction, surface codes, or repetition codes are crucial for practical deployment. Comparison with classical ASIC mining hardware shows promising energy efficiency, but scalability remains a critical factor for practical application. As quantum hardware advances toward fault-tolerant systems, this research provides a valuable foundation for energy-efficient cryptocurrency mining in the quantum era.
5. Code Implementation
Quantum CNOT gate implementation
# Quantum XOR (CNOT) implementation for SHA-256Quantum SHA-256 compression function pseudocode
function quantum_sha256_compress(message_block, current_hash):6. Future Applications
Quantum SHA-256 implementation opens several future application pathways:
- Hybrid quantum-classical mining farms: Integrating quantum processors with classical mining infrastructure for gradual transition
- Quantum-Safe Cryptocurrency: Development of novel cryptocurrency specifically designed for quantum hardware
- Green Blockchain Initiative: Environmental Sustainable Blockchain Network Using Quantum Energy Efficiency
- Post-Quantum Cryptography Mining: Adapting to Cryptocurrency Mining with Quantum-Resistant Algorithms
Future research directions include optimizing quantum circuit depth, developing error mitigation strategies for noisy quantum devices, and exploring quantum annealing methods for cryptocurrency mining.
7. Manazarta
- Nielsen, M. A., & Chuang, I. L. (2010). Quantum Computation and Quantum Information. Cambridge University Press.
- Ablayev, F., & Vasiliev, A. (2014). Cryptographic quantum hashing. Laser Physics Letters, 11(2), 025202.
- IBM Quantum Experience. (2023). IBM Quantum Processor Specifications. IBM Research.
- Google Quantum AI. (2022). Quantum Supremacy Using a Programmable Superconducting Processor. Nature, 574(7779), 505-510.
- National Institute of Standards and Technology. (2022). Post-Quantum Cryptography Standardization. NIST.
- Orun, A., & Kurugollu, F. (2023). Quantum SHA-256 Implementation for Energy-Efficient Cryptocurrency Mining. Journal of Quantum Computing and Cryptography.
- Merkle, R. C. (1978). Secure communications over insecure channels. Communications of the ACM, 21(4), 294-299.
- Diffie, W., & Hellman, M. (1976). New directions in cryptography. IEEE Transactions on Information Theory, 22(6), 644-654.